Source: The Register
Itanic sinks further beneath the waves
The Linux kernel will no longer support Intel Itanium processors following a decision by Linus Torvalds to merge a patch marking the architecture as orphaned.…
Source: The Register
The Linux kernel will no longer support Intel Itanium processors following a decision by Linus Torvalds to merge a patch marking the architecture as orphaned.…
Source: Hacker News
Source: Hacker News
Source: Saturday Morning Breakfast Cereal

Hovertext:
If anyone's having deja vu, this was run in Nautilus magazine a while back. I'm linking to the amazon page where you can buy.
Source: Hacker News
Source: The Week: Most Recent Home Page Posts

"The discovery of highly transmissible coronavirus variants in the United States has public health experts urging Americans to upgrade the simple cloth masks that have become a staple shield during the pandemic," The Washington Post reports. Dr. Anthony Fauci, the nation's top infectious disease expert, suggested on Monday's NBC Today that people consider wearing two masks at the same time, explaining, "If you have a physical covering with one layer, you put another layer on, it just makes common sense that it likely would be more effective."
Experts suggest wearing a surgical mask underneath a cloth mask, assuming you don't have access to N95 or KN95 masks, which afford the most protection. Linsey Marr, an engineering professor at Virginia Tech and mask effectiveness researcher, told the Post that if you don't have access to surgical masks, you can create a protective three-layer mask by sandwiching a high-efficiency filter — like one cut from a vacuum bag — between two tightly woven fabric masks.
The Centers for Disease Control and Prevention (CDC) advises Americans to wear a tight-fitting masks with "two or more layers of washable, breathable fabric," and to leave surgical masks and N95 respirators for health care workers. Fauci appeared alongside new CDC Director Rochelle Walensky at a CNN town hall on Wednesday and advised people to follow the CDC guidelines. Walensky said N95s are uncomfortable and might turn people off of wearing masks entirely.
Many other countries have responded to the contagious new variants by mandating that people wear medical-grade masks in public — Europe's solution — or by mass-producing high-quality masks and shipping them directly to residents, as South Korea, Singapore, and other Asian nations have done, the Post reports. Some medical experts — and The Week's Ryan Cooper — say the Biden administration should consider following Asia's lead.
All available evidence "suggests two masks are likely more effective than a single mask," and "in situations where you are not able to social distance, you may want to double up by wearing a cloth mask over a surgical mask or two cloth masks," Jamie Ueda writes at Reviewed. But "if you already have trouble breathing while wearing one mask, adding another may not be the best option. The CDC notes wearing one mask is better than not wearing any face covering."
Source: Hacker News
Source: Ars Technica
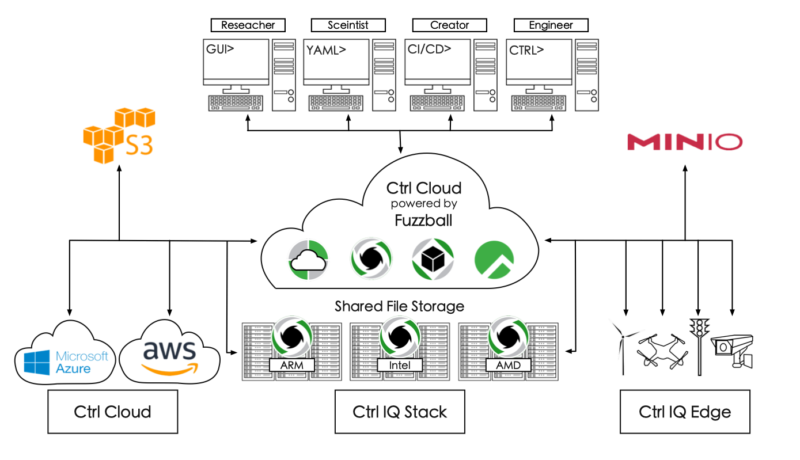
Enlarge / Ctrl IQ provided us with this diagram of its proposed technology stack. (Thankfully, spelling correction is not one of the core services Ctrl IQ offers.) (credit: Ctrl IQ)
Gregory Kurtzer, co-founder of the now-defunct CentOS Linux distribution, has founded a new startup company called Ctrl IQ, which will serve in part as a sponsoring company for the upcoming Rocky Linux distribution.
Rocky Linux is to be a beneficiary of Ctrl IQ's revenue, not its source—the company describes itself in its announcement as the suppliers of a "full technology stack integrating key capabilities of enterprise, hyper-scale, cloud and high-performance computing."
If you've been hiding under a Linux rock for the last few months, CentOS Linux was the most widely known and used clone of Red Hat Enterprise Linux. Kurtzer co-founded CentOS Linux in 2004 with mentor Rocky McGaugh, and it operated independently for 10 years until being acquired by Red Hat in 2014. When Red Hat killed off CentOS Linux in a highly controversial December 2020 announcement, Kurtzer immediately announced his intention to recreate CentOS with a new distribution named after his deceased mentor.
Source: Hacker News
Source: The Register
Analysis So it seems 2021 is going to be the year that internet culture finally reaches the deepest and most protected pockets of society.…